Category: Software
-

DALL-E 3: wow
DALL-E 3 is here. And the future too, or almost at least. Prompt: generate 3D images of the inside of a house in Singapore. It needs to look modern and minimalistic, with light colours, to show a customer. Focus on the living room. It still sucks at generating text… Trying to get an 80s style…
-

RPi kernels in Bookworm
Raspberry Pi recently launched Bookworm, and with that, a new kernel package. However, due to the massive changes from Bullseye to Bookworm, they are not suggesting a dist-upgrade. In the past, we have suggested procedures for updating an existing image to the new version, but always with the caveat that we do not recommend it,…
-

IP Changed?
Very simple Python script that tracks one or multiple hosts/domains for IP changes, and prints it in a Matrix room. Includes a Docker container to keep it running. I made it less noisy (i.e. won’t talk when the IP didn’t change) and as the IP of my DynDNS hosts hasn’t changed yet, there’s not much…
-

Check websites with LanguageTool for typos
This is quick and dirty (and with the help of ChatGPT). FlatTurtle has a new site, and there’s been some fine-tuning here and there that led to a few typos creeping in. I wanted a quick tool to plug in a page, and that would highlight possible mistakes. I’ve been a personal (paying) user of…
-

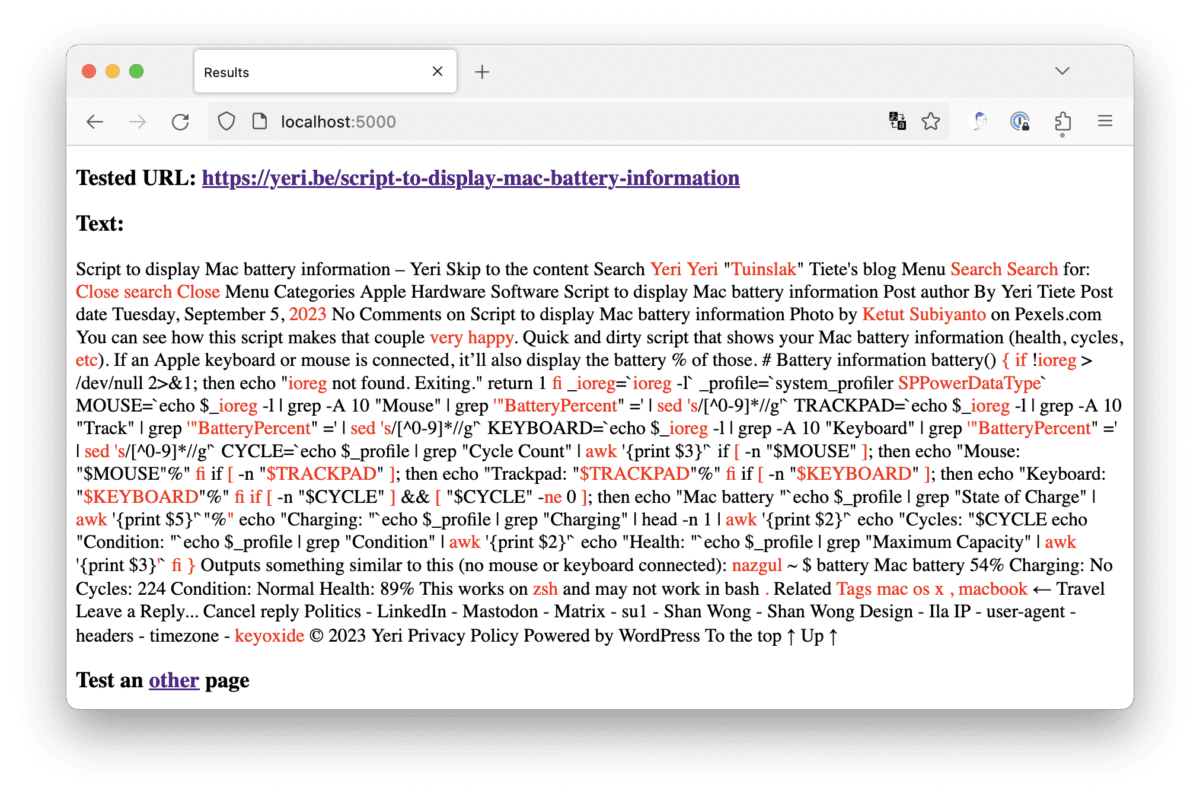
Script to display Mac battery information
You can see how this script makes that couple very happy. Quick and dirty script that shows your Mac battery information (health, cycles, etc). If an Apple keyboard or mouse is connected, it’ll also display the battery % of those. Outputs something similar to this (no mouse or keyboard connected): This works on zsh and…
-

PoC: Betteruptime + Python-kasa
Content Update The provided scripts have been updated on 16 Jul 2023. Specifically the SmartStrip part was not working as intended. I’ve been a big fan of Betteruptime. I’ve started using it to monitor all my assets online (websites, DNS, ping, successful script runs) as well as my servers (using heartbeats). I have a few…
-

killwarp
Is your company forcing Cloudflare Warp on you, and are you running on a Mac (with sudo access)? It probably sucks, spies on you, does MitM attacks, breaks most video conferencing tools, and is generally not very stable… Also… Zero trust! Add this function to your .bashrc or .zshrc (whichever shell you’re using*): Open a…
-

Don’t trust corporates
Especially those at the pinnacle that’ve lost touch with their customers. I’ve blogged about it before. Here is how platforms die: first, they are good to their users; then they abuse their users to make things better for their business customers; finally, they abuse those business customers to claw back all the value for themselves.…
-

Bookworm: eth0 -> enX0
Started updating my Debian systems from Bullseye to Bookworm. The first thing I noticed was that ethX renamed to enXY. To get back to the old naming scheme, you can fix this by adding the following in /etc/network/interfaces: And reboot.