Category: Networking
-
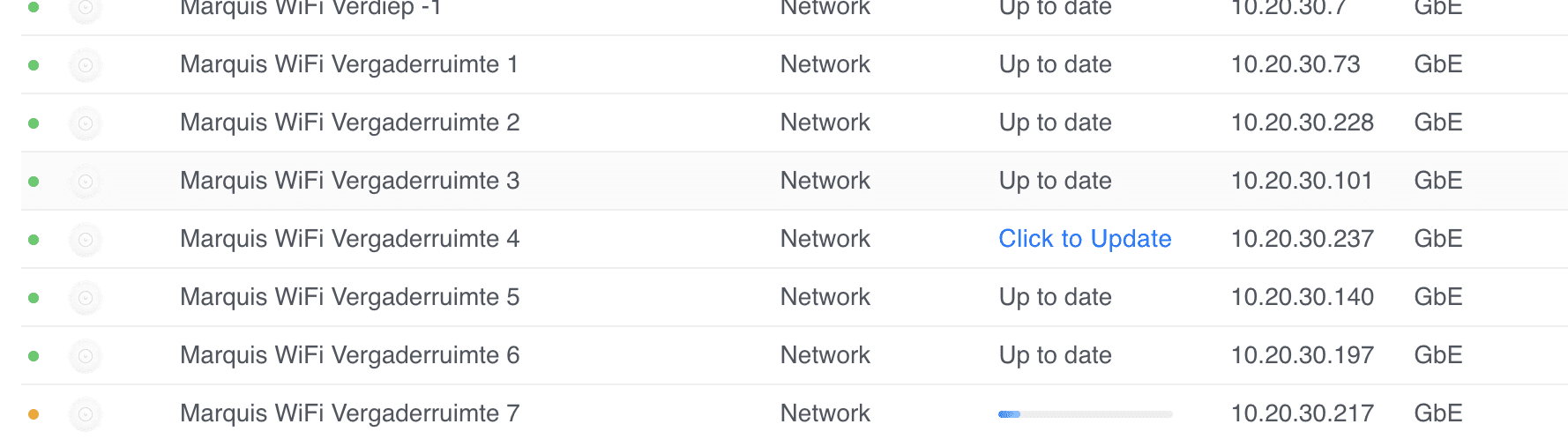
Unifi u6+ failing to upgrade
I have quite a few sites where some Unifi U6+ Access Points fail to upgrade with a generic update failed message. Marquis WiFi Vergaderruimte 4 update failed. I’ve tried everything, from ssh‘ing, factory resetting with set-default, to manually upgrading with upgrade, etc. Nothing worked. I thought I had a bunch of bad APs (and many…
-

The Future is here
Never have any cell signal in parking spaces in Belgium, but at least now we (and the cars) have WiFi! 🙂 Another 8 buildings connected (including outdoor WiFi in the park, and in the shared indoor spaces).
-

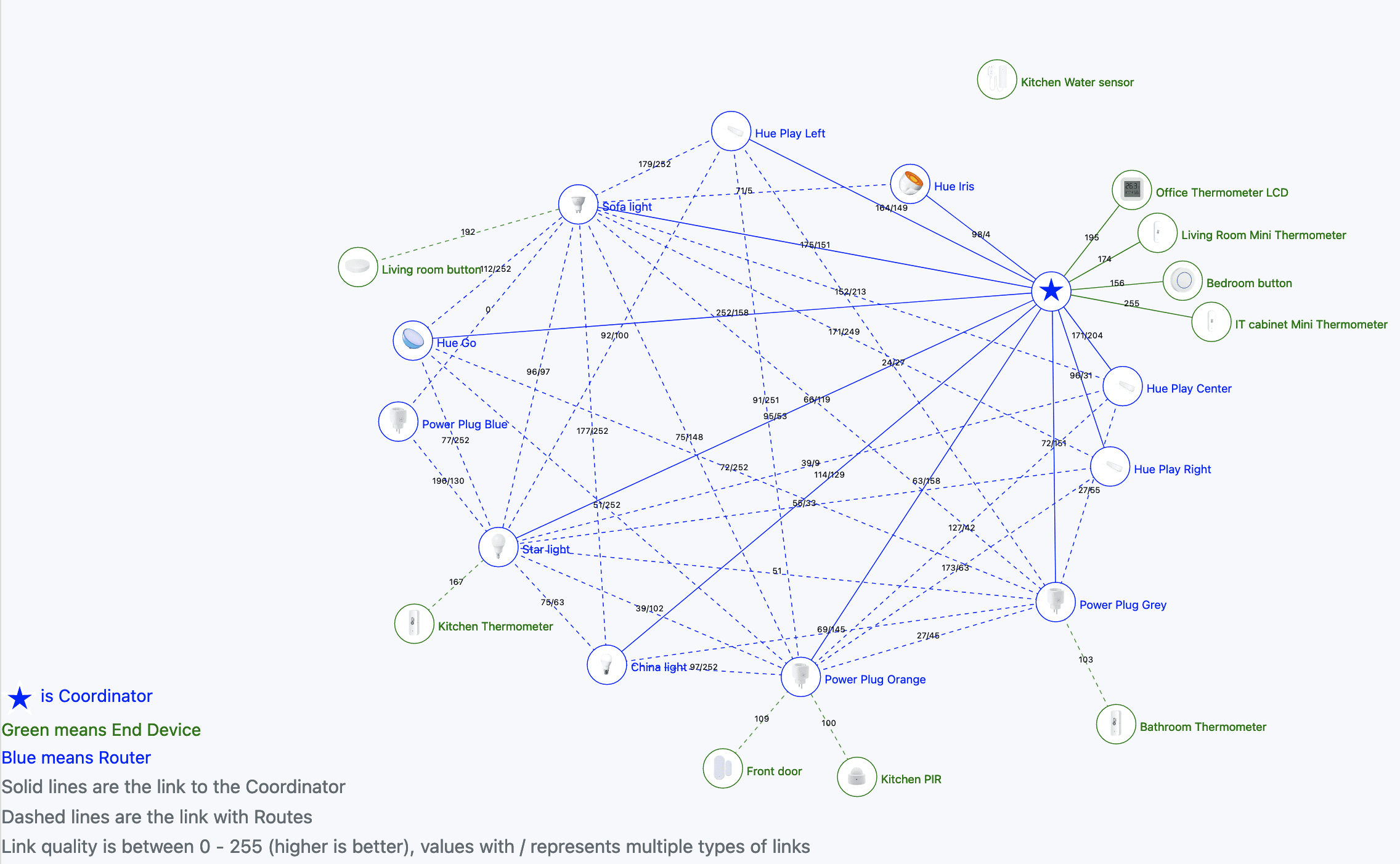
Home Assistant: Zigbee routers
In my Home Assistant quest and simplifying (not sure if that’s actually happening) and getting more control (aka less reliant on the cloud and 3rd parties) I’ve been playing with Zigbee. Zigbee is quite cool because it’s a mesh network. As I used it before with my Philips Hue bulbs, I was eager to expand…
-

Home Assistant: Getting rid of Philips Hue bridge
In my Home Assistant quest and simplifying (not sure if that’s actually happening) and getting more control (aka less reliant on the cloud and 3rd parties) I’ve been playing with Zigbee. Zigbee is quite cool because it’s a mesh network. As I used it before with my Philips Hue bulbs, I was eager to expand…
-

Home Assistant: ESP32-C3 Bluetooth proxy
I have set up an ESP32-c3 Bluetooth Proxy for a Mi ble thermometer (and I have a few other BLE sensors that I haven’t managed to set up yet). The proxy config can be found here. Be sure to modify the variables to match whatever you want to do. I’m using static IPs because auto…
-

IP Changed?
Very simple Python script that tracks one or multiple hosts/domains for IP changes, and prints it in a Matrix room. Includes a Docker container to keep it running. I made it less noisy (i.e. won’t talk when the IP didn’t change) and as the IP of my DynDNS hosts hasn’t changed yet, there’s not much…
-

PoC: Betteruptime + Python-kasa
Content Update The provided scripts have been updated on 16 Jul 2023. Specifically the SmartStrip part was not working as intended. I’ve been a big fan of Betteruptime. I’ve started using it to monitor all my assets online (websites, DNS, ping, successful script runs) as well as my servers (using heartbeats). I have a few…
-

killwarp
Is your company forcing Cloudflare Warp on you, and are you running on a Mac (with sudo access)? It probably sucks, spies on you, does MitM attacks, breaks most video conferencing tools, and is generally not very stable… Also… Zero trust! Add this function to your .bashrc or .zshrc (whichever shell you’re using*): Open a…
-

Bookworm: eth0 -> enX0
Started updating my Debian systems from Bullseye to Bookworm. The first thing I noticed was that ethX renamed to enXY. To get back to the old naming scheme, you can fix this by adding the following in /etc/network/interfaces: And reboot.