Tag: wifi
-
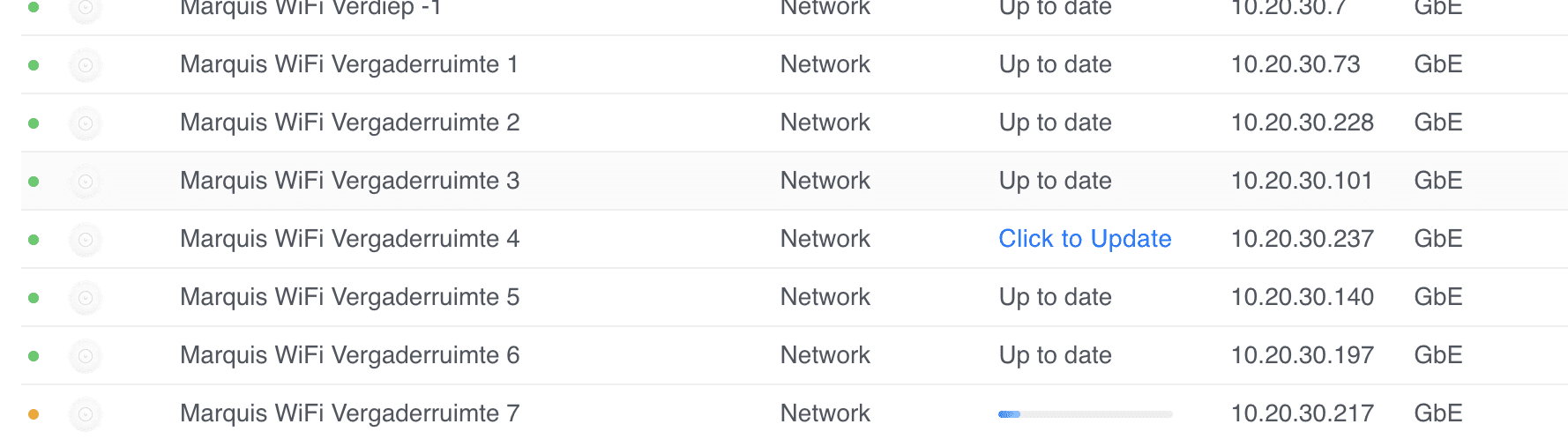
Unifi u6+ failing to upgrade
I have quite a few sites where some Unifi U6+ Access Points fail to upgrade with a generic update failed message. Marquis WiFi Vergaderruimte 4 update failed. I’ve tried everything, from ssh‘ing, factory resetting with set-default, to manually upgrading with upgrade, etc. Nothing worked. I thought I had a bunch of bad APs (and many…
-

The Future is here
Never have any cell signal in parking spaces in Belgium, but at least now we (and the cars) have WiFi! 🙂 Another 8 buildings connected (including outdoor WiFi in the park, and in the shared indoor spaces).
-

Ideal travel router: GL-AR750S
Right. With the pandemic and all none of us are going to travel much but still… About a year ago I purchased myself an OpenWRT router to use on the plane and in hotels. And so far I really like both the device and the Hong Kong based brand (launching new and updated products, and…
-
EVA and WiFi
So I am flying EVA from SIN – TPE – JFK and back. For the first time I also went to the dark side (16hrs was too long to be locked up with just my mind) and got onboard WiFi. This seems to come with unlimited data for ~20USD for 24hrs. I manage to stream…
-
WiFi by night
-
FlatTurtle in elevators: making of
First tests at Glaverbel (circle or “O” shaped building) in Watermael-Boisfort with 12 lifts (about a year ago). Internet wiring makes a whole circle from the internet connection at the technical room (near entrance hall). In this design from the 1960s the lift machine rooms had one shared/common room where we installed switches (to avoid…
-
Turtle shaped WiFi
demolished a unifi from Auki and build a 3D printed Turtle around it. Came out very nicely, and it’s quite solid. 3D renders: Actual printed design: Opened up unifi: Design by Seendesign. More at FlatTurtle’s blog.
-
Outdoor WiFi (120onCortenbergh)
About a year later… Except not being white anymore, it still looks good. Outdoor unifi (previous model) connected to Auki. Picture enhanced by Google Plus to add dramatic effect. 😉 Original picture here.
-
Outdoor WiFi (Pegasus Park)
Point to Point transmitters (Loco M2) Point to Point receiver (Loco M2) Boxes with power, PoE and switches Outdoor Access Point (UAP Outdoor+)

