Tag: router
-

Ideal travel router: GL-AR750S
Right. With the pandemic and all none of us are going to travel much but still… About a year ago I purchased myself an OpenWRT router to use on the plane and in hotels. And so far I really like both the device and the Hong Kong based brand (launching new and updated products, and…
-

NextDNS, EdgeOS and device names
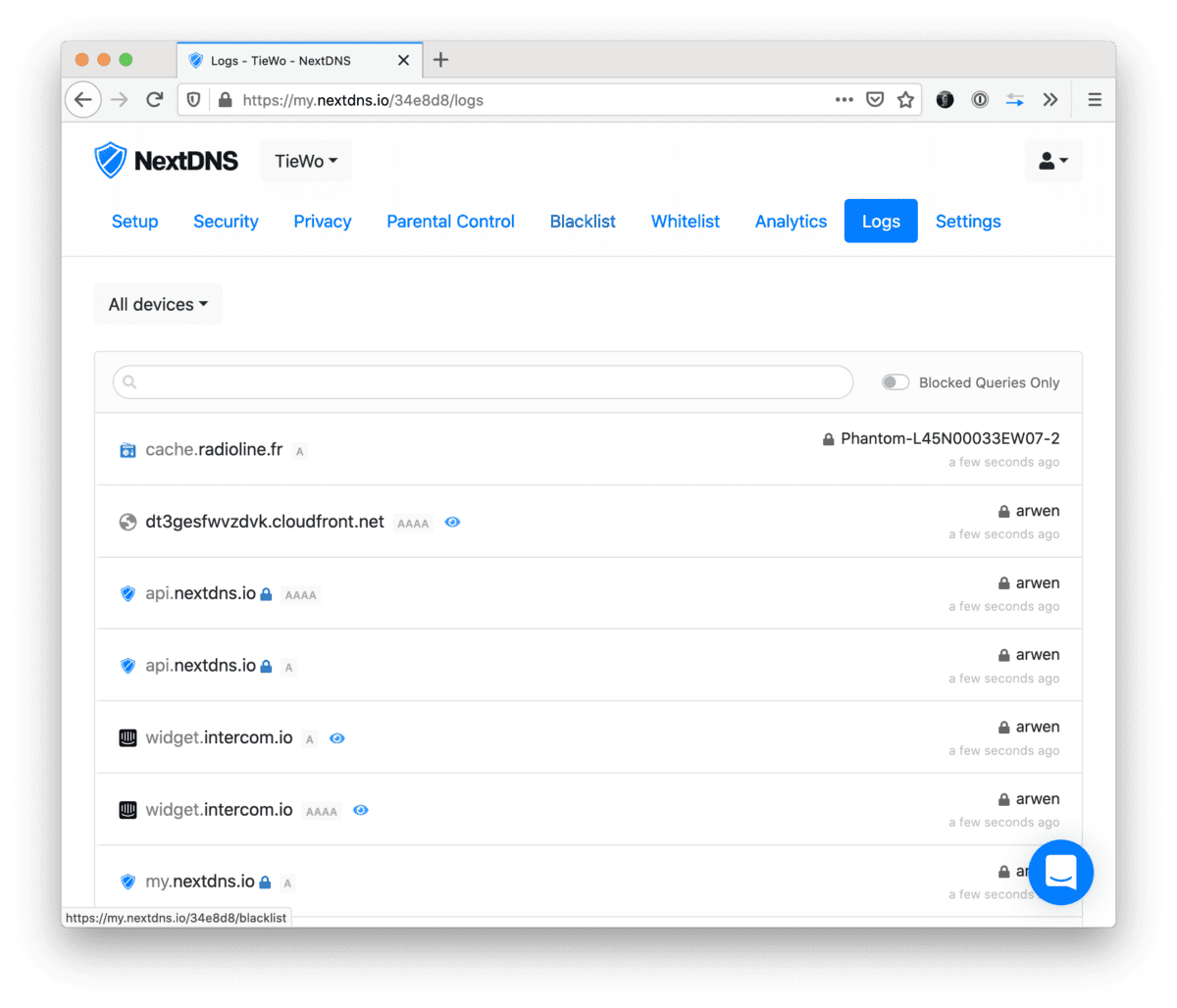
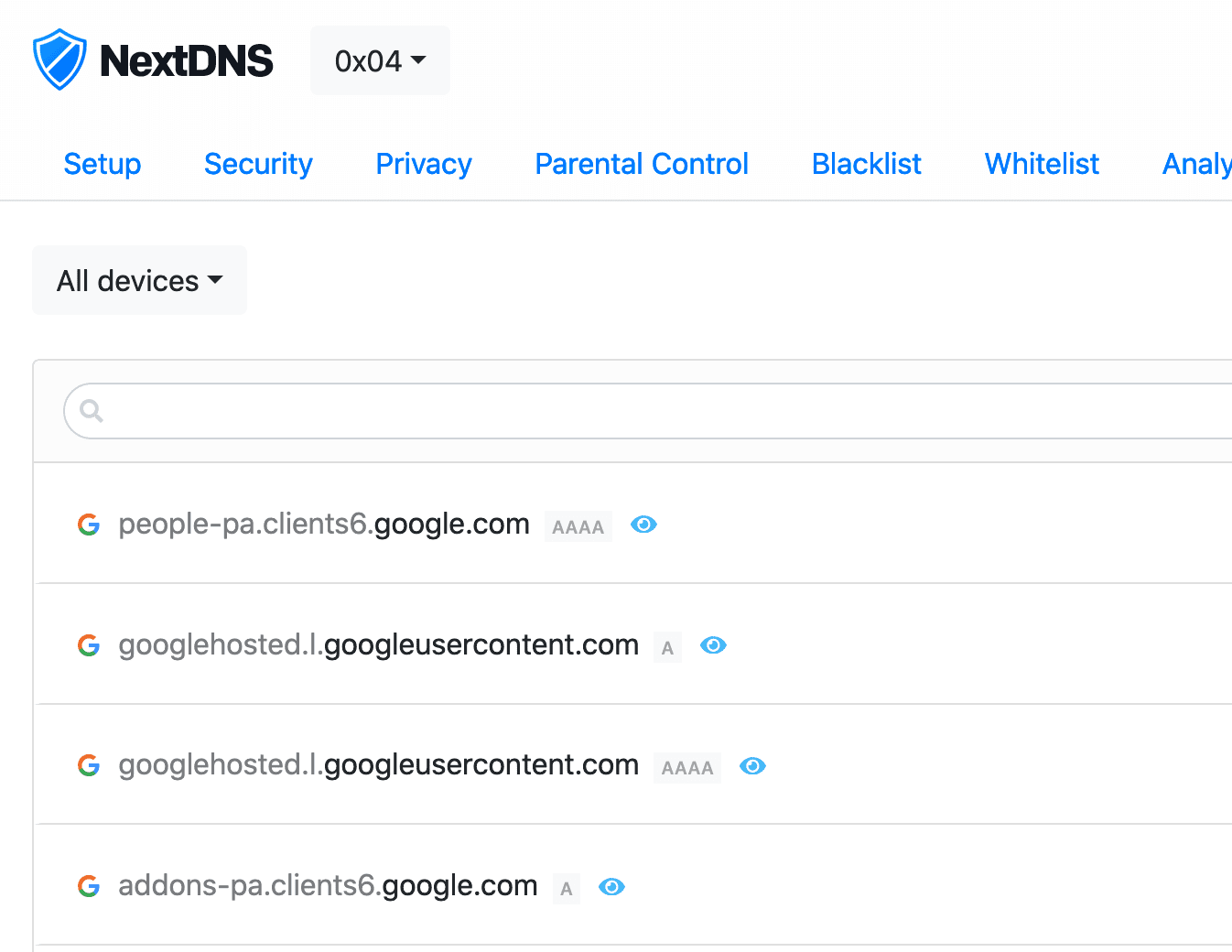
Noticed that NextDNS was reporting old hostnames in the logs. For example old device names (devices that changed hostnames), devices that were definitely no longer on the network, or IPs that were matched to the wrong hostnames. The culprit is how EdgeOS deals with its hosts file. Basically it just keeps all the old hosts…
-

NextDNS + EdgeRouter + Redirecting DNS requests
Realised I haven’t updated this in a long while (life happened). Couple of weeks ago I started to play with NextDNS — and I really recommend anyone that’s something privacy minded and cares about the stuff happening on their network. I’ve set up several configs (home, parents, FlatTurtle TurtleBox (the NUCs controlling the screens)) and…
-
Linux gateway/router + unable to access certain (HTTPS) sites
I’ve had an issue for a while, being unable to access certain websites such as https://fon.com, but also certain parts of the Apple, Fortis and Microsoft site, while other (https) websites worked fine. Running Wireshark I found that only about 5ish packets got transferred, and all other data to that website abruptly stopped. I’m using…