Tag: rootspirit
-
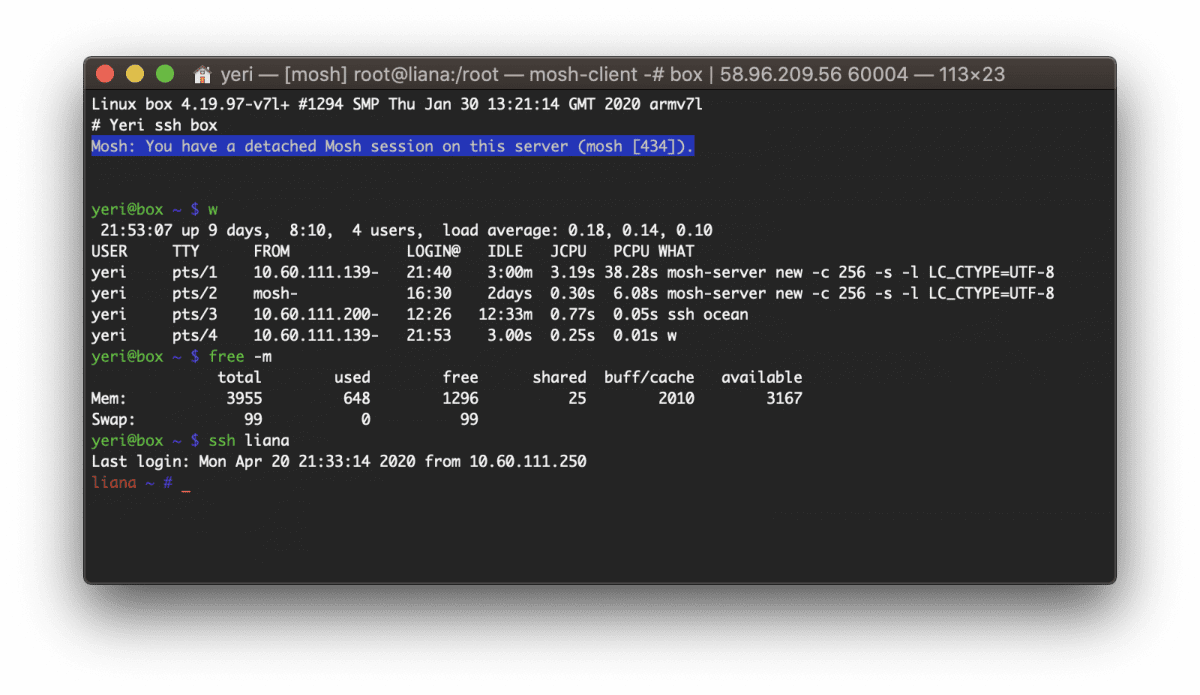
Box — Docker shell server
A couple of months ago I had the great idea to set up a shell server in Docker. Simply because my docker skillz were quite rusty and a shell server was something I actually genuinely needed. Shell servers… so 2005. I remember in the good old IRC days people asking for (free) shell servers to…
-
Postfix & Courier & Letsencrypt
First of all, create your certificates (the regular way). I created one with multiple domains: webmail.rootspirit.com, mail.rootspirit.com, smtp.rootspirit.com. In my case, as the mailserver and webserver are behind a proxy (postfix, imap, Roundcube Webmail), I create the certificate on the proxy (nginx) and scp the cert to the mail server. All this is automated with…
-
Gmail & Postfix: unencrypted emails?
If you’re running Postfix, add this line to main.cf: smtp_tls_security_level = may Restart Postfix, and retry. PS: You can set encrypt instead of may — but this can cause issues with Amavis and/or SpamAssassin.
-
Theme
I had the same theme for over four years. I’ve made quite a few custom css and PHP edits myself, and it had been outdated for ages… But it served me well. However, it’s now time for something new. As always, as minimalistic as possible. On a side note, this blog has been moved from…
-
Blog’s back
Yay, after some hardware issues my blog’s back. Zero had a corrupt reiserfs. Decommissioned the old P4 and replaced by a brand new dual Xeon. Running Xen and Debian instead of Gentoo. And shortly there after Four (the server that hosts this VM), the Ubuntu host with Xen refused to start its networking, so I decided to start a fresh…
-
One
Oh lord. I seem to have entirely forgotten One’s, euh, uptime-day. (Yea, blame my business trips in Beijing & San Francisco for that). But… Over 2 years! yay
-
Theme, blog, and stuff
As you noticed… Or perhaps didn’t notice, I’ve started using a new, simplistic theme a couple of days ago. Kinda thought it might be too simplistic (I’ve hidden the sidebar, there’s no search or archive, etc), but I started to, you know, get attached to it. So it’s here to stay, for a year or…
-
Zero
Big grats to good old Zero and its one year uptime! 😉
-
Four
Has a year uptime as well! Yay 😉 It’s the one at the bottom. Running Ubuntu as OS (Dom0) and several Xen virtual machines (such as the nginx reverse proxy cache of this blog). Four is a dual core Xeon with 8Gb RAM.