Tag: raspberrypi
-
RPi kernels in Bookworm
Raspberry Pi recently launched Bookworm, and with that, a new kernel package. However, due to the massive changes from Bullseye to Bookworm, they are not suggesting a dist-upgrade. In the past, we have suggested procedures for updating an existing image to the new version, but always with the caveat that we do not recommend it,…
-

NextDNS and NetworkManager
A while back, I wrote about installing NetworkManager if NextDNS activate fails to work. Only… I realised that for some reason on Raspberry Pi (4), WiFi stopped working with the following errors: The WiFi SSID and password (wpa_supplicant) never changed, so I wasn’t sure what it was. However, as most Pi’s are wired I didn’t…
-

Mounting a whole disk with partitions
I reinstalled one of my RPis (moving from 32 to 64 bit). Before doing the full reinstall, I took a dump (dd) of my disk. Usually, I create one per partition, but this was the Christmas season, and I was half occupied with feasting and half occupied with entertaining Ila. So, mistakes were made. I…
-
OLED Lego Brick
Via Hackaday.
-

NetworkManager exit status 1
Recently reinstalled NextDNS on a RPi4 64bit and came across this error: It seems like NextDNS was actually running, but just throwing an error when running nextdns activate. Restarting did seem to work without throwing any error. The logs showed the same error: The solution was (as root): Looks like, instead of resolvconf, openresolv was…
-

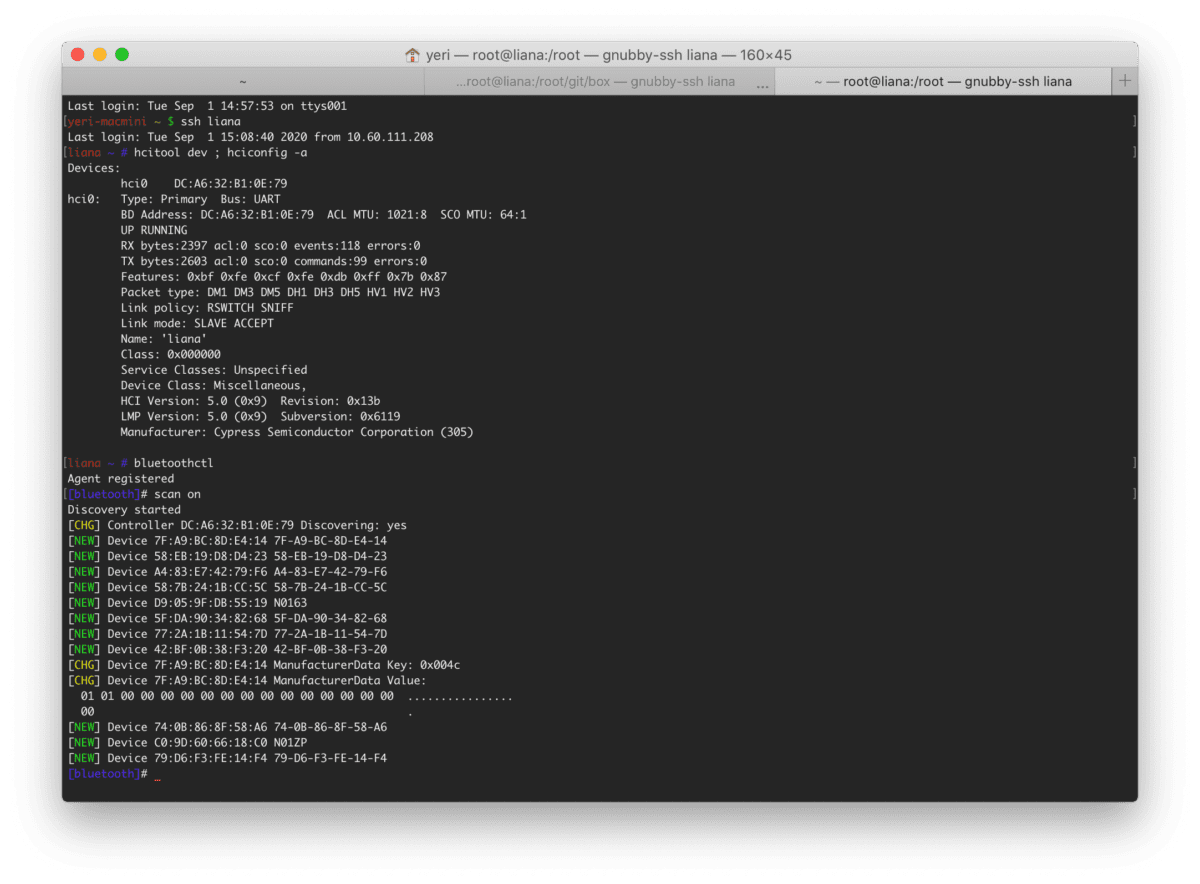
Making Bluetooth work on RPi4
I rarely use Bluetooth on my RPis. I’m already facing enough issues with my iMac and Mac Mini (it lags, it randomly disconnects in meetings, etc). My pwnagotchi on the other hand is counting on a BLE network to connect to the internet: for now I am using my iPad, and while that works, it…
-

Raspberry Pi 4 + SSD
All right. With the release of the new RPi4 with 8Gb of RAM I had to get myself one to see if it was already a viable desktop replacement for surfing and emails. While a SD card works fine for certain tasks (things that don’t require a lot of IO) — for a desktop that’s…
-

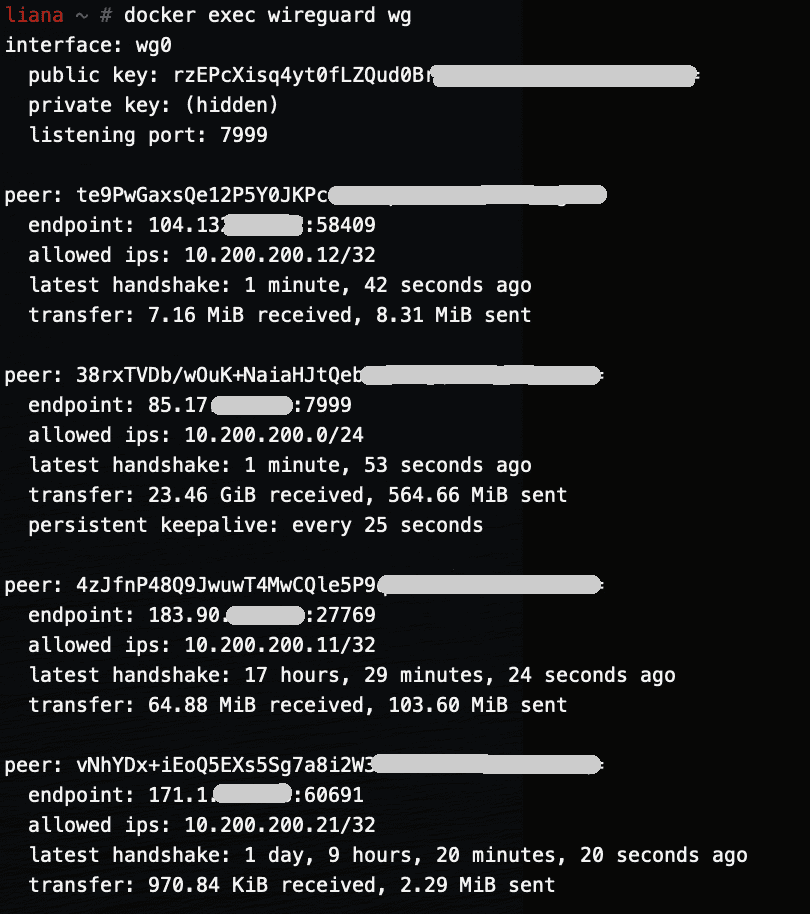
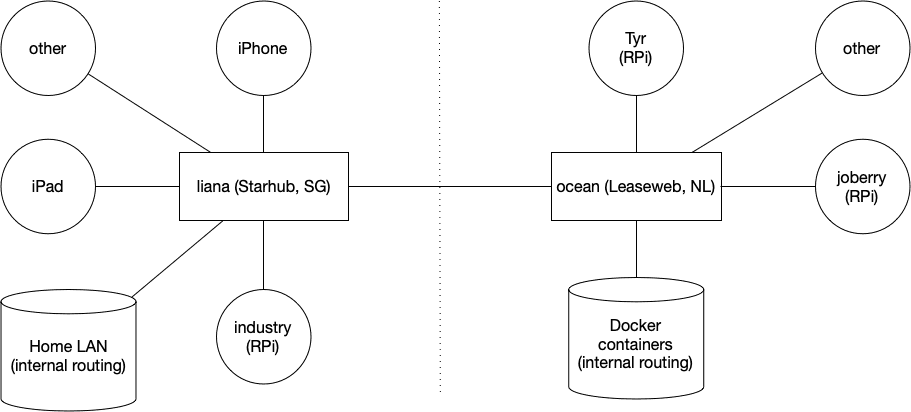
Running WireGuard in a Docker container (RPi)
This follows the my two other posts about WireGuard. Most of this can be copied from the amd64 post — with a minor change for making it work on RPi4. This is the full git repo (including both rpi and amd64). The main difference is in the run.sh file. The installation is a bit different…
-

WireGuard
This is the first post of several. Next posts will focus on running WireGuard inside a Docker container on amd64 Linux and a Raspberry Pi. I’ve been running WireGuard for a few months now and I’ve been loving it. I first started using it about a year ago when in China — OpenVPN was once…