Tag: docker
-

PoC: Betteruptime + Python-kasa
Content Update The provided scripts have been updated on 16 Jul 2023. Specifically the SmartStrip part was not working as intended. I’ve been a big fan of Betteruptime. I’ve started using it to monitor all my assets online (websites, DNS, ping, successful script runs) as well as my servers (using heartbeats). I have a few…
-

Feed2Toot
Started looking into a service to auto-post from this blog onto my Mastodon feed. Feed2Toot fit the bill perfectly. I wanted to run the whole thing from a Docker container, though, so I’ll quickly write a how-to. This whole thing runs from a Raspberry Pi, as root. No k8s or k3s for me. The path…
-

Smokeping.eu
I’ve revamped my Smokeping infra a bit since 2020. First off, starting to use the smokeping.eu1 domain that Bianco got 10 or so years ago instead of using weird URLs under superuser.one domain. It’s running on four nodes as we speak: a virtual machine on a colocation server in Leaseweb, Amsterdam, NL -> leaseweb.nl.smokeping.eu a…
-

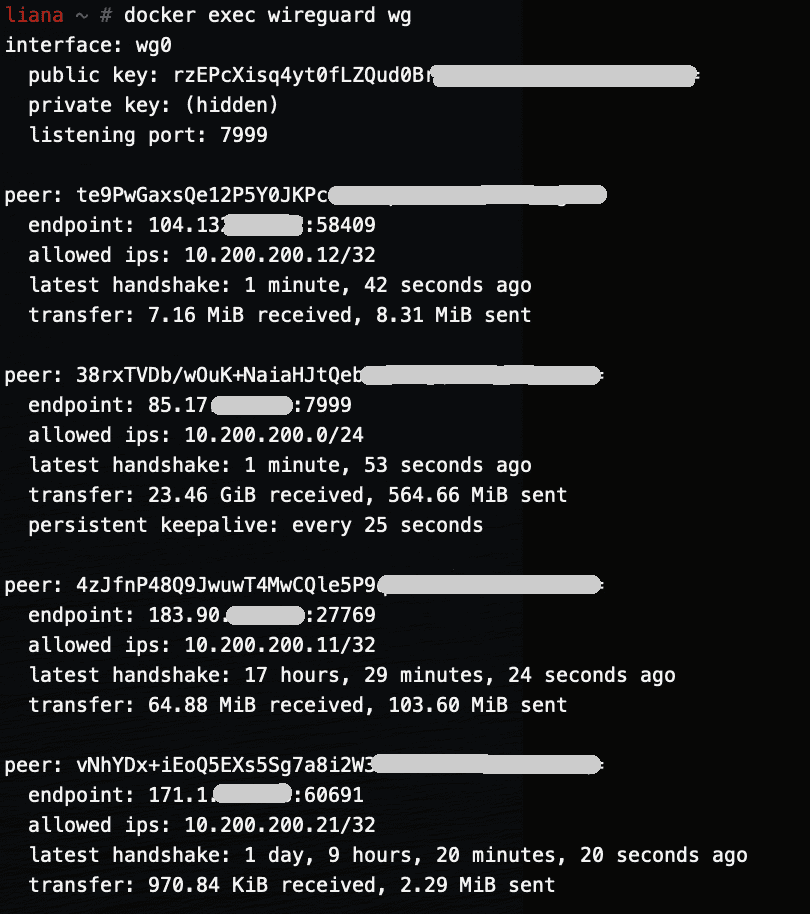
Running WireGuard in a Docker container (RPi)
This follows the my two other posts about WireGuard. Most of this can be copied from the amd64 post — with a minor change for making it work on RPi4. This is the full git repo (including both rpi and amd64). The main difference is in the run.sh file. The installation is a bit different…
-

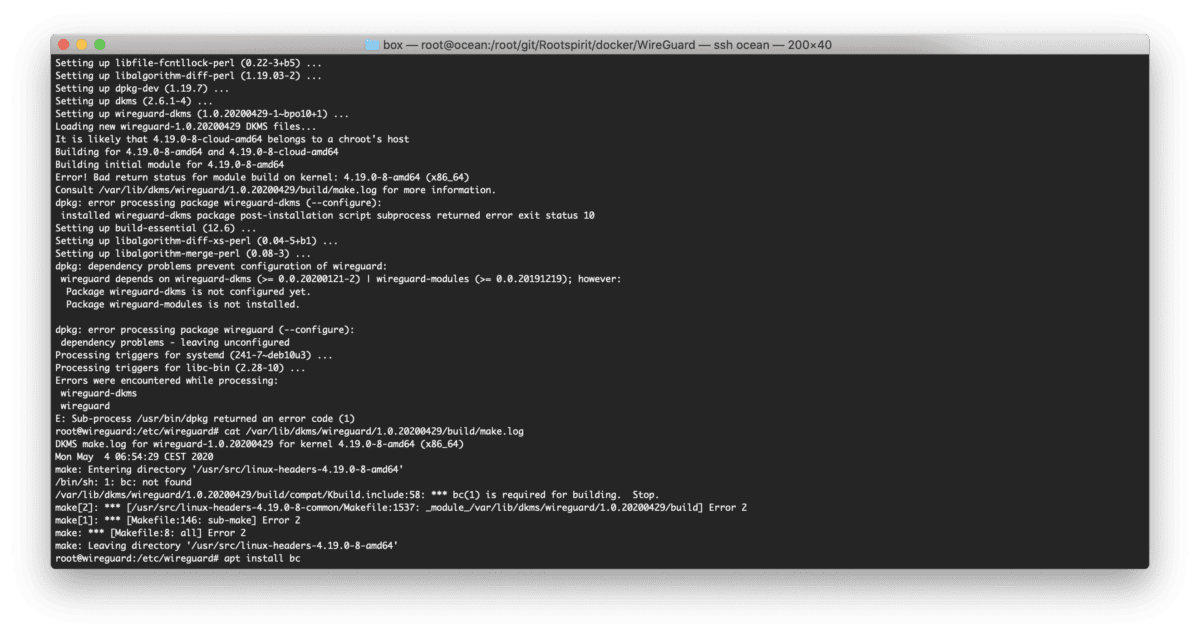
Error! Bad return status for module build on kernel: 4.19.0-8-amd64 (x86_64)
I was rebuilding my WireGuard Docker container today and this error started popping up: The solution was to install bc. Seems like Debian is not pulling the right dependencies. I’ll be adding it to my Dockerfile.
-

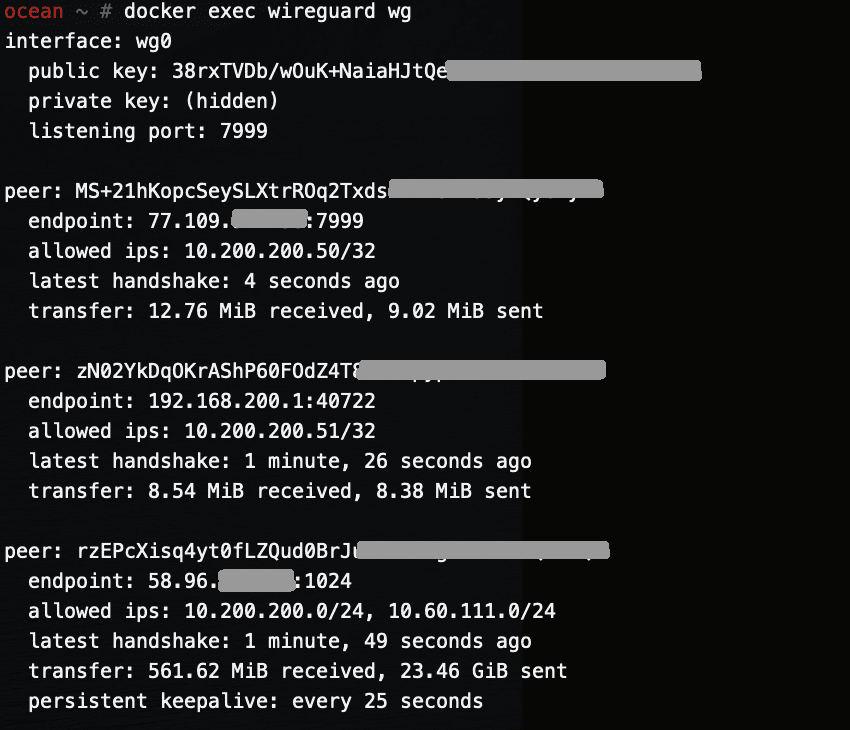
Running WireGuard in a Docker container (amd64)
This is the 2nd post about WireGuard. So I am running two WireGuard servers — one on a Raspberry Pi 4, and one in an amd64 virtual machine. This post will be about getting WireGuard working on amd64 in a Docker container. As this container rarely get rebuild, I am running unattended-upgrades inside the container…
-

WireGuard
This is the first post of several. Next posts will focus on running WireGuard inside a Docker container on amd64 Linux and a Raspberry Pi. I’ve been running WireGuard for a few months now and I’ve been loving it. I first started using it about a year ago when in China — OpenVPN was once…
-

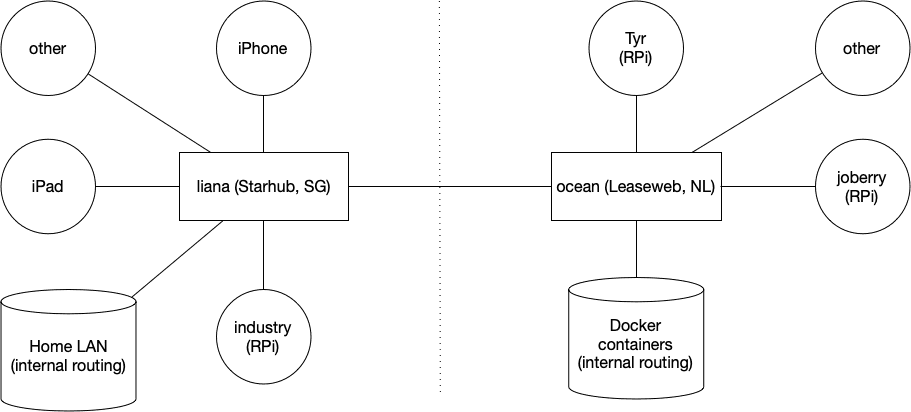
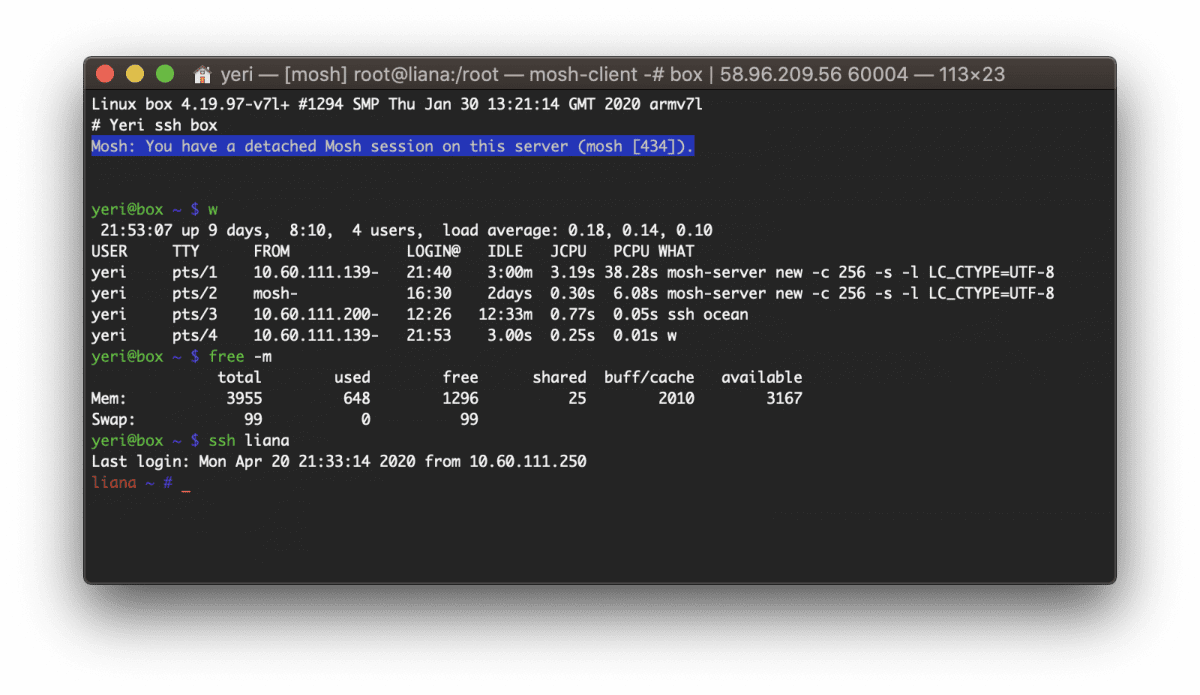
Box — Docker shell server
A couple of months ago I had the great idea to set up a shell server in Docker. Simply because my docker skillz were quite rusty and a shell server was something I actually genuinely needed. Shell servers… so 2005. I remember in the good old IRC days people asking for (free) shell servers to…