Category: www
-
FlatTurtle blog
After letting our blog gather dust since 2015, I’m excited to announce a fresh start. 😉 We’ve been busy with other projects, but now we’ve exported all our content from Tumblr and transitioned to a Hugo static site. This is my first time working with Hugo, and I must say, it’s quite impressive. I’m using…
-

WordPress unable to connect to SQL database
Yesterday, three blogs I’m hosting suddenly went offline and alerts went off. They all had the same error that they couldn’t connect to their SQL database, and it seemed that the container recently was auto-updated. Docker logs also showed (which may or may not have been related): This was odd. I started the usual troubleshooting:…
-

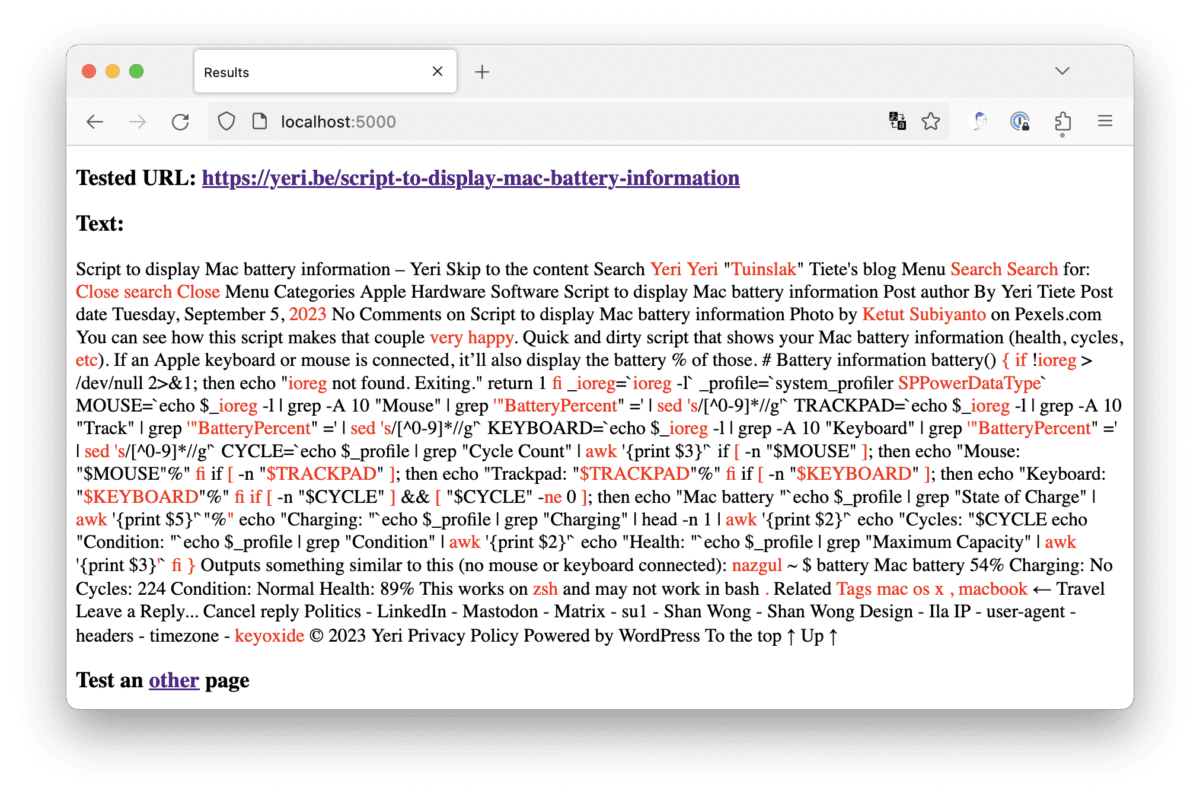
Check websites with LanguageTool for typos
This is quick and dirty (and with the help of ChatGPT). FlatTurtle has a new site, and there’s been some fine-tuning here and there that led to a few typos creeping in. I wanted a quick tool to plug in a page, and that would highlight possible mistakes. I’ve been a personal (paying) user of…
-

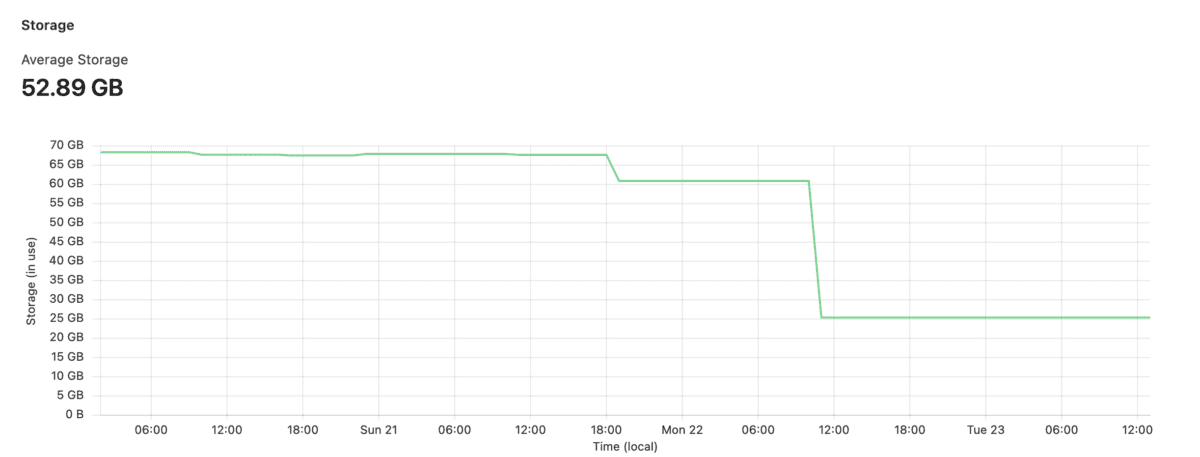
Keeping Mastodon storage in check
For my Mastodon instance, I use Cloudflare R2; mainly for two reasons: While I didn’t care much about storage any more, I still wanted to make sure it was kept in check, also for two reasons: I run my Mastodon in a Docker instance, so your commands may vary (basically tootctl X Y is what…
-

Kagi
It’s now been roughly 6 months I’ve switched from DuckDuckGo to Kagi. I started paying right away after roughly the one month trial. I had not been very happy with DDG; mostly the results were very low quality (having to switch back to Google one too many times; results often lagged behind by months of…
-

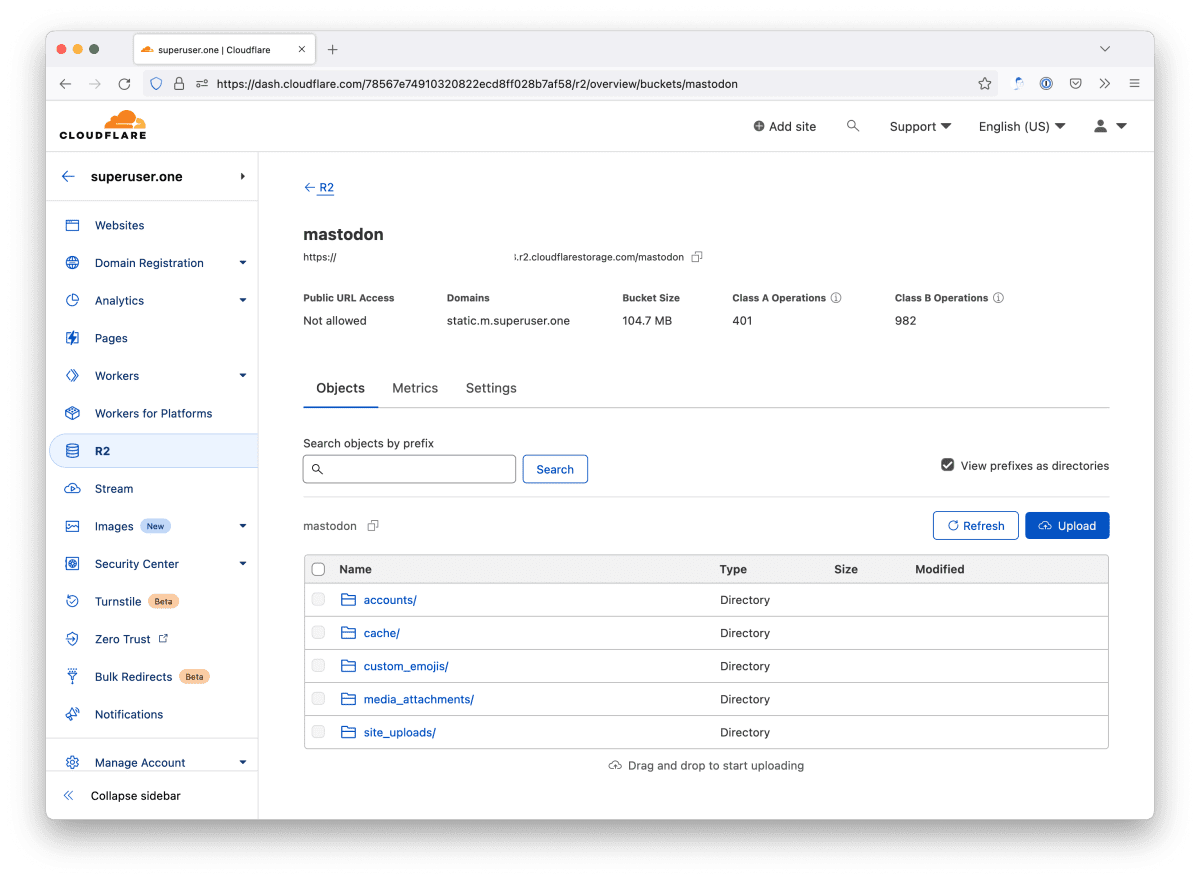
Mastodon server: R2
This is a very short post because to be honest, I didn’t figure much out myself. My uploads/static files are now saved in R2 under its own URL (part of my enterprise zone) so that my normal caching rules and other settings are applied. Add these to your application.env file: The token/API key is a…
-

Using Mastodon with Cloudflare
If you’re using Mastodon with Cloudflare CDN/protection and minify turned on, you’ll notice the site may look broken (after a few visits, when hitting Cloudflare cache). And you’ll notice errors in the webdev tools similar to Failed to find a valid digest in the ‘integrity’ attribute, with computed SHA-256 integrity: Basically, the sha256 hash doesn’t…
-

Remote desktop and Wake-on-LAN
Shan uses her iPad a lot, but a lot of the more serious (interior design) work needs to happen on AutoCAD or Photoshop. That is just not going to work on an iPad. When we’re travelling (read: holiday) she’s carrying an old Lenovo ThinkPad 13 (great device!) just “in case” she needs to open AutoCAD…
-

Facebook content moderation
On Monday, an AP reporter tested how the company would respond to a similar post on Facebook, writing: “If you send me your address, I will mail you abortion pills.” The post was removed within one minute. The Facebook account was immediately put on a “warning” status for the post, which Facebook said violated its…