Category: Linux
-
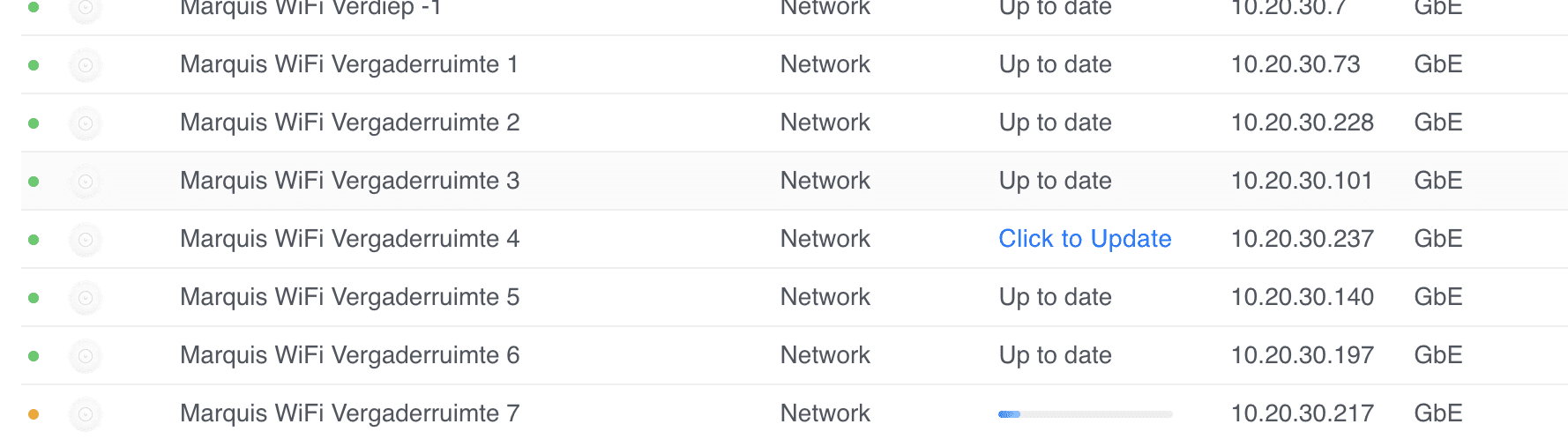
Unifi u6+ failing to upgrade
I have quite a few sites where some Unifi U6+ Access Points fail to upgrade with a generic update failed message. Marquis WiFi Vergaderruimte 4 update failed. I’ve tried everything, from ssh‘ing, factory resetting with set-default, to manually upgrading with upgrade, etc. Nothing worked. I thought I had a bunch of bad APs (and many…
-

GTFS
As iRail’s servers go down once in a while (and contain some legacy files, making it a bit messy), I decided to back up and host the GTFS feeds of Belgian Railway (NMBS), and the 3 Belgian bus companies (De Lijn, TEC and MIVB) at gtfs.flatturtle.cloud. Every night, around 3am (CET), the GTFS files are…
-

WordPress unable to connect to SQL database
Yesterday, three blogs I’m hosting suddenly went offline and alerts went off. They all had the same error that they couldn’t connect to their SQL database, and it seemed that the container recently was auto-updated. Docker logs also showed (which may or may not have been related): This was odd. I started the usual troubleshooting:…
-

RPi kernels in Bookworm
Raspberry Pi recently launched Bookworm, and with that, a new kernel package. However, due to the massive changes from Bullseye to Bookworm, they are not suggesting a dist-upgrade. In the past, we have suggested procedures for updating an existing image to the new version, but always with the caveat that we do not recommend it,…
-

PoC: Betteruptime + Python-kasa
Content Update The provided scripts have been updated on 16 Jul 2023. Specifically the SmartStrip part was not working as intended. I’ve been a big fan of Betteruptime. I’ve started using it to monitor all my assets online (websites, DNS, ping, successful script runs) as well as my servers (using heartbeats). I have a few…
-

Bookworm: eth0 -> enX0
Started updating my Debian systems from Bullseye to Bookworm. The first thing I noticed was that ethX renamed to enXY. To get back to the old naming scheme, you can fix this by adding the following in /etc/network/interfaces: And reboot.
-

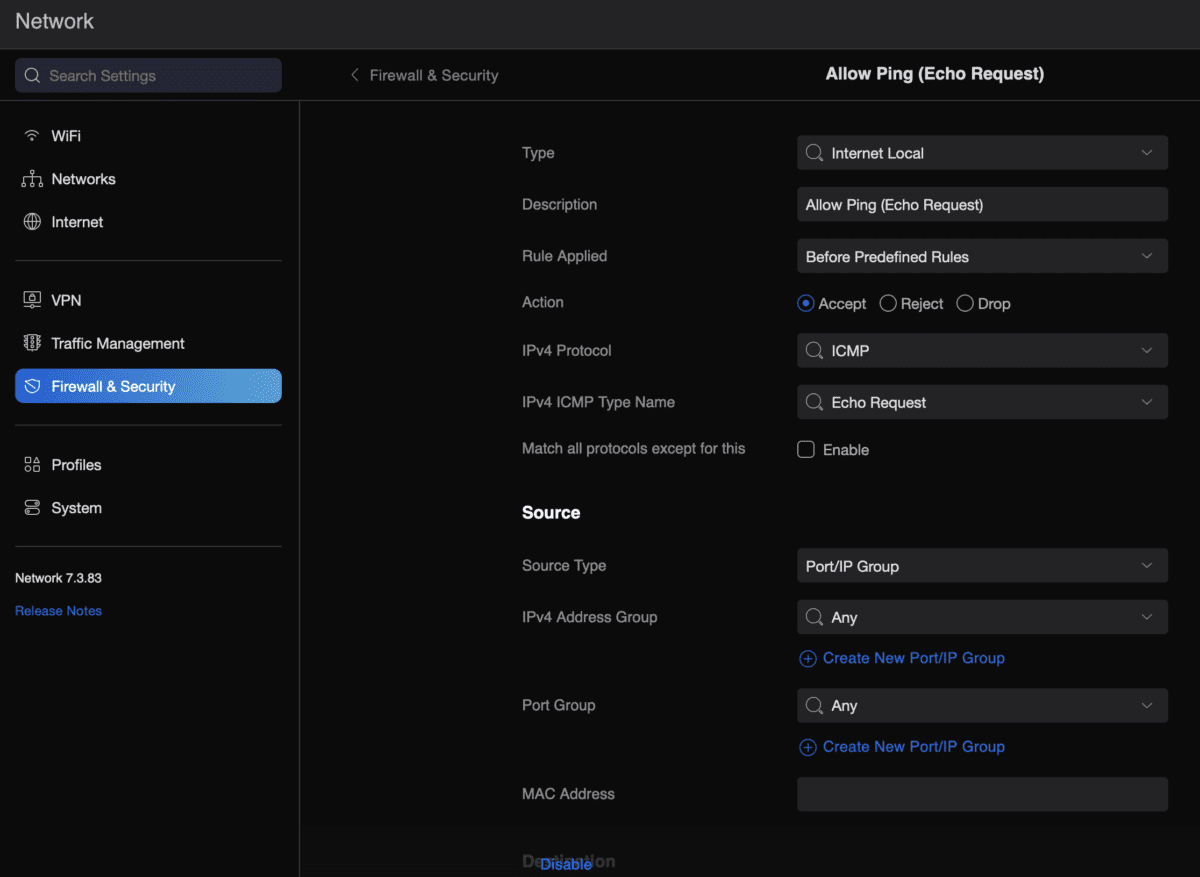
Allow ping from USG
Because I keep forgetting and it takes me far too much time to go through one of my million sites where I set this up and find the right config… To allow a USG (Unifi Security Gateway) to reply to external (WAN) ping requests, do the following: That’s it… All this for Smokeping.
-

NextDNS and NetworkManager
A while back, I wrote about installing NetworkManager if NextDNS activate fails to work. Only… I realised that for some reason on Raspberry Pi (4), WiFi stopped working with the following errors: The WiFi SSID and password (wpa_supplicant) never changed, so I wasn’t sure what it was. However, as most Pi’s are wired I didn’t…
-

Mounting a whole disk with partitions
I reinstalled one of my RPis (moving from 32 to 64 bit). Before doing the full reinstall, I took a dump (dd) of my disk. Usually, I create one per partition, but this was the Christmas season, and I was half occupied with feasting and half occupied with entertaining Ila. So, mistakes were made. I…